At Slim.AI, we constantly monitor containers for security issues, both for our customers and for approximately 500 of what we deem to be the world’s most popular public containers. So when major vulnerabilities come to the fore — as happened two weeks ago when cURL, one of the world’s most popular and ubiquitous dev tools, announced a HIGH severity vulnerability — we naturally ask the question: Who’s fixed this and who hasn’t?
In the case of CVE-2023-38545, which cURL maintainers dubbed “the worst security issue we’ve seen in curl in a long time”, what we found was both promising and a bit scary. Two weeks later, despite major distros having patched the vulnerability quickly and the security community making sure it was no secret via social media, some 33-percent of the world’s most popular public containers still haven’t been updated.

Remediating the vulnerability is as simple as updating your cURL version to 8.4, yet several containers in our dataset have failed to do so. Initially, we discovered 103 vulnerable images out of the approximately 500 images we track on a regular basis across multiple public image registries. That is to say, these 103 contained a vulnerable version of cURL in their latest version that was flagged by open source scanners Grype and Trivvy that we use for analysis.
Just one day later, 39-percent of those images had been fixed, with Slim’s container profiling system detecting new versions of cURL (8.4) and open source vulnerability scanners Grype and Trivvy no longer recording the CVE.
Over the course of two weeks, another 29 public images took in the updates. Considering most public container images follow a 1-day or 7-day update cycle, meaning in two weeks, most should have already patched this issue.
So why do we still see so many images still impacted by CVE-2023-38545? And what does that mean for your security profile?

For those who don’t know, cURL is probably the most used and one of the most loved Linux dev tools on the planet. It was released the same year (1996) as Space Jam and the Spice Girls’s debut album, Spice, if that means anything to you.
cURL is used by developers to make HTTP requests, useful for say, pinging websites, testing API endpoints, or downloading assets. Its “bottle opener”-level utility means that it is commonly included in container base images as a convenience for developers.
Less commonly, developers actually NEED cURL in their containers to perform certain functions. While having a tool that can make HTTP calls to the open internet gives most DevSecOps teams a tingling feeling on the back of their necks, production environments are often locked down to prevent outbound traffic and have other controls. These types of production configurations have a big impact on the “exploitability” of a given CVE.
Still, best practice would dictate that once dev and testing suites are completed, cURL should be removed if it isn’t being used by the production application. Zero-day vulnerabilities such as CVE-2023-38545 provide a textbook case for why shipping only what you need to production is a container best practice.

It should be said that the disclosure of this vulnerability was well done. The cURL maintainers made it known to the community that an important vulnerability — “the worst security issue we’ve seen in curl in a long time”, they wrote — was coming in the 8.4 patch and that users should upgrade immediately.
It should also be said that while the CVE was rated as a High, the relative exposure was relatively low. Remember:
This vulnerability required certain configurations to be present (use of the SOCKS5 proxy), and experts estimated that only a small number of users would be exposed. In fact, in our analysis of these containers, we did not find a single instance of where cURL would be reachable within the container (that is to say, there was no application code that explicitly called cURL based on Slim’s proprietary profiling analysis).

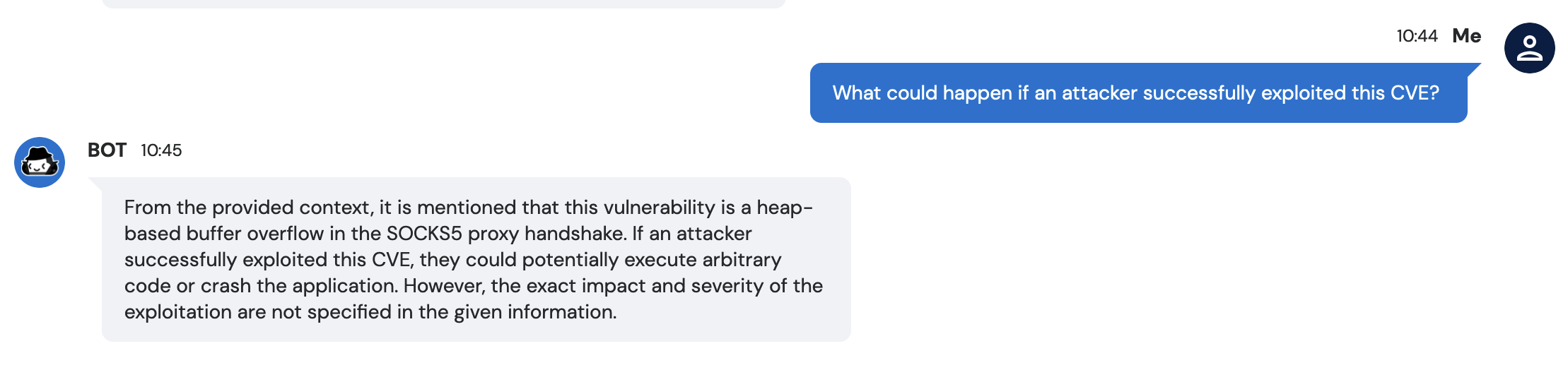
Still, the impact of the vulnerability being exploited is dire, according to experts. At Slim, we’ve recently launched to customers a “CVE Chatbot” that can answer questions about CVE information — it is, naturally, based on an LLM. According to our “Codi P.I.” bot: 'If an attacker successfully exploited this CVE, they could potentially execute arbitrary code or crash the application.'
So if this CVE was such a big deal, why do we still see so many popular public images that are still impacted? There are plenty of reasons, some more valid than others.
At Slim, we’re working hard to eliminate the friction that comes with vulnerability remediation. Here are some reasons these images may not be fixed, and how Slim is working to make these blockers easier for teams to manage, whether you are the one using the image or the one maintaining it.
Our goal for this article was not to “name and shame” containers whose versions of cURL are out of date. We’ve reached out directly to maintainers of those container images where we could to notify them.
Container vulnerability scanner technology — including the engines we host on Slim.AI — are sufficient to detect the outdated versions. If you are concerned about your containers, login to Slim and start scanning your own containers today.
Want to manage vulnerability remediation and cURL updates more effectively? Join our beta to get access to our collaborative workspaces for vulnerability management.

We're excited to share some big news from Slim.AI. We're taking a bold new direction, focusing all our energy on software supply chain security, now under our new name root.io. To meet this opportunity head-on, we’re building a solution focused on transparency, trust, and collaboration between software producers and consumers.
When we started Slim.AI, our goal was to help developers make secure containers. But as we dug deeper with our early adopters and key customers, we realized a bigger challenge exists within software supply chain security — namely, fostering collaboration and transparency between software producers and consumers. The positive feedback and strong demand we've seen from our early customers made it crystal clear: This is where we need to focus.
This new opportunity demands a company and brand that meet the moment. To that end, we’re momentarily stepping back into stealth mode, only to emerge with a vibrant new identity, and a groundbreaking product very soon at root.io. Over the next few months, we'll be laser-focused on working with design partners and building up the product, making sure we're right on the mark with what our customers need.
Stay informed and up-to-date with our latest developments at root.io. Discover the details about the end of life for Slim services, effective March 31, 2024, by clicking here.

We're excited to share some big news from Slim.AI. We're taking a bold new direction, focusing all our energy on software supply chain security, now under our new name root.io. To meet this opportunity head-on, we’re building a solution focused on transparency, trust, and collaboration between software producers and consumers.
When we started Slim.AI, our goal was to help developers make secure containers. But as we dug deeper with our early adopters and key customers, we realized a bigger challenge exists within software supply chain security — namely, fostering collaboration and transparency between software producers and consumers. The positive feedback and strong demand we've seen from our early customers made it crystal clear: This is where we need to focus.
This new opportunity demands a company and brand that meet the moment. To that end, we’re momentarily stepping back into stealth mode, only to emerge with a vibrant new identity, and a groundbreaking product very soon at root.io. Over the next few months, we'll be laser-focused on working with design partners and building up the product, making sure we're right on the mark with what our customers need.
Stay informed and up-to-date with our latest developments at root.io. Discover the details about the end of life for Slim services, effective March 31, 2024, by clicking here.